Security Architecture: Built on Zero-Trust Principles
Vaultix implements military-grade security architecture designed to protect your digital assets against every known attack vector. Our zero-trust security model ensures your private keys never leave the physical device-no exceptions.
Foundation: Five Security Layers
Vaultix security architecture is built on five independent layers of protection, each providing defense-in-depth against different threat models.
Layer 1: Hardware Security
Secure Element chip with cryptographic co-processor. Tamper-resistant casing with physical intrusion detection. Military-grade component selection.
Layer 2: Firmware Security
Open-source firmware auditable by security community. Cryptographically signed updates with rollback protection. Minimal attack surface design.
Layer 3: Cryptographic Security
Industry-standard encryption algorithms (AES-256, SHA-256). Hardware random number generation. Secure key derivation (BIP32/BIP39/BIP44).
Layer 4: Air-Gap Isolation
Complete offline operation for key storage and transaction signing. No internet connectivity required. Physical confirmation for all operations.
Layer 5: Recovery Security
Encrypted seed phrase backup with optional passphrase. Multiple recovery methods with redundancy. No cloud storage-complete user control.
Secure Element Chip: Your Keys' Fortress
At the heart of Vaultix is a dedicated Secure Element (SE) chip-the same technology used in passports, credit cards, and government ID systems. This specialized cryptographic processor is designed for one purpose: protecting sensitive data against physical and logical attacks.
What is a Secure Element?
A Secure Element is a tamper-resistant microprocessor chip that stores cryptographic keys and performs cryptographic operations in an isolated, protected environment. Unlike general-purpose processors, SE chips are specifically hardened against:
- Side-channel attacks: Protection against power analysis, electromagnetic emissions, and timing attacks
- Fault injection: Resistance to voltage glitching, clock manipulation, and laser attacks
- Physical tampering: Self-destruct mechanisms if invasive probing is detected
- Software exploits: Isolated execution environment prevents malware access
Planned Technical Specifications
| Certification Target: | Common Criteria EAL5+ or EAL6+ |
| Cryptographic Algorithms: | AES-256, SHA-256, ECDSA, RSA |
| Random Number Generator: | True hardware RNG (TRNG) |
| Key Storage: | Isolated secure memory, keys never exposed |
Offline Transaction Signing: Air-Gap Protection
Vaultix signs transactions completely offline, ensuring your private keys never touch an internet-connected device. This air-gapped workflow provides maximum security against remote attacks.
Create Unsigned Transaction
Use Vaultix companion app (desktop or mobile) to construct transaction details: recipient address, amount, network fee. The app runs on your internet-connected computer but never has access to your private keys.
Transfer to Vaultix Device
Connect Vaultix hardware wallet via USB or scan QR code containing unsigned transaction data. Device displays transaction details on secure screen for your verification. Vaultix remains offline-no internet connection required.
Sign and Broadcast
After physical confirmation on device, Vaultix signs transaction using private key stored in Secure Element. Signed transaction returns to companion app for broadcast to blockchain network. Private key never leaves the device.
Security Guarantee
Because transaction signing occurs entirely within the isolated Secure Element chip, even if your computer is compromised by malware, attackers cannot steal your private keys or modify transaction details without your physical confirmation on the Vaultix device screen.
Air-Gapped Architecture: Complete Isolation
An air gap is a physical separation between your private keys and any internet-connected system. This isolation makes remote attacks impossible.
❌ Hot Wallet (Internet-Connected)
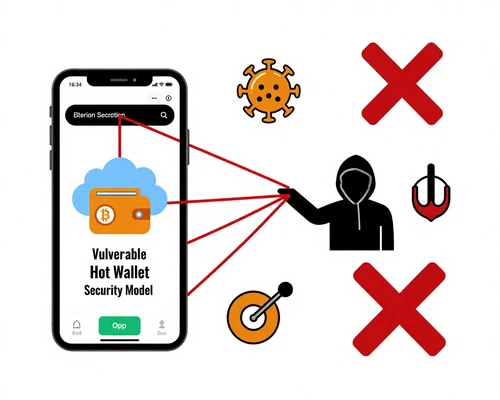
- Private keys stored on internet-connected device
- Vulnerable to malware, keyloggers, remote access trojans
- Susceptible to phishing attacks and clipboard hijacking
- Server breaches can expose keys if custodial wallet
- No physical confirmation required for transactions
✓ Vaultix (Air-Gapped)

- Private keys stored offline in Secure Element chip
- No internet connectivity-impossible to attack remotely
- Physical confirmation required on device for all transactions
- Malware on computer cannot access keys or alter transactions
- Complete user control-no custodian, no third party
Encrypted Recovery System: Never Lose Access
Vaultix uses industry-standard BIP39 seed phrase recovery, enhanced with optional BIP39 passphrase encryption for maximum security. Your recovery phrase is the master key to your digital assets-protecting it is critical.
How Recovery Works
During initial setup, Vaultix generates a cryptographically secure 24-word seed phrase using the device's hardware random number generator. This seed phrase mathematically derives all your private keys and can restore your wallet on any BIP39-compatible device.
Two-Layer Recovery Security
Layer 1: Seed Phrase (24 words)
Write down your 24-word seed phrase on the provided recovery card. Store it securely in a physical location (safe, safety deposit box). Never store digitally or photograph-physical-only backup prevents remote theft.
Layer 2: Optional Passphrase (25th word)
Add an additional passphrase (sometimes called the "25th word") that encrypts your seed phrase. Even if someone steals your 24-word recovery card, they cannot access your funds without this memorized passphrase. This creates plausible deniability-a different passphrase generates a completely different wallet.
⚠️ Critical Recovery Rules
- Never store seed phrase digitally: No photos, no cloud storage, no password managers
- Use metal backup for long-term storage: Paper degrades; metal survives fire water
- Test your recovery: Verify you can restore wallet before transferring large amounts
- Multiple secure locations: Store backup copies in geographically separate locations
- Passphrase security: If using 25th word, ensure you'll remember it-no way to recover forgotten passphrase

Open-Source Firmware: Transparency by Design
Vaultix will release open-source firmware, enabling independent security audits by the global cryptography community. Transparency builds trust-you shouldn't have to trust us blindly.
Why Open Source Matters for Security
Closed-source security is "security by obscurity"-relying on attackers not knowing how your system works. This fails when source code leaks or reverse engineering succeeds. Open-source security follows Kerckhoffs's principle: a system should remain secure even if everything except the key is public knowledge.
github.com/vaultix-wallet/firmware
│
├── /src
│ ├── secure_element.c # SE chip interface
│ ├── transaction_signing.c # Offline signing logic
│ ├── recovery.c # BIP39 seed management
│ ├── display.c # Secure screen rendering
│ └── crypto/
│ ├── aes256.c # Encryption implementation
│ ├── sha256.c # Hashing functions
│ └── ecdsa.c # Digital signatures
│
├── /tests # Unit & integration tests
├── /docs # Architecture documentation
└── /audits # Third-party security reportsOpen-Source Security Benefits
- Community Verification: Thousands of security researchers can review code for vulnerabilities
- No Backdoors: Impossible to hide malicious code in publicly auditable firmware
- Reproducible Builds: Anyone can compile firmware and verify it matches the version running on device
- Long-Term Support: Community can maintain firmware even if Vaultix company ceases operation
- Standards Compliance: Pursuing OSHWA (Open Source Hardware Association) certification
Verification Process (Post-Launch)
- Download Vaultix firmware source code from official GitHub repository
- Review cryptographic implementations and security-critical functions
- Compile firmware from source using provided build instructions
- Compare cryptographic hash of your compiled firmware to device firmware hash
- Verify digital signature on firmware update using Vaultix public key
Zero Data Collection: No Telemetry, No KYC, No Tracking
Vaultix implements a zero-knowledge architecture. We cannot see your balances, transaction history, or even which cryptocurrencies you hold. Your financial privacy is absolute.
No Telemetry
Vaultix firmware contains zero analytics, crash reporting, or usage tracking. The device never phones home. We don't know how many wallets you've created, how often you transact, or which features you use. Complete operational privacy.
No KYC
No identity verification required to purchase or use Vaultix. No name, address, government ID, or personal information collected. Pseudonymous ordering process protects your privacy from purchase through usage. Your identity is your business.
No Tracking
We don't log IP addresses, device fingerprints, or transaction patterns. Companion apps communicate directly with blockchain nodes-no Vaultix servers intermediating connections. We cannot correlate wallet addresses to real-world identities or usage patterns.
No Cloud
Zero cloud dependencies. Your private keys, seed phrases, transaction history, and wallet metadata never sync to any server. Everything stays local on your device. Even if Vaultix servers shut down permanently, your wallet continues functioning without interruption.
Our Privacy Philosophy
Most hardware wallet companies collect extensive telemetry under the guise of "improving user experience." We believe your transaction patterns, portfolio holdings, and financial behavior are none of our business. We've architected Vaultix to make surveillance technically impossible-even if legally compelled, we cannot provide data we don't collect.
Keys Never Leave Device - Guaranteed
This is the fundamental security promise of hardware wallets, and Vaultix enforces it through hardware isolation.
Your private keys are generated inside the Secure Element chip during initial setup using a hardware random number generator. From that moment forward, the private keys never leave the SE chip-not to the device's main processor, not to the companion app, not to any external system.
When you sign a transaction, the unsigned transaction data is sent into the Secure Element, signed internally using the isolated private key, and only the signed transaction (not the key) is returned. This architecture makes private key extraction physically impossible without destroying the chip.
Even Vaultix cannot access your keys. If you lose your device and recovery phrase, your funds are permanently inaccessible-there is no "reset password" or customer support recovery. This is the tradeoff for true self-custody: ultimate security requires ultimate responsibility.
Third-Party Security Audits: Coming Soon
Vaultix will undergo comprehensive third-party security audits before public launch. We're engaging independent cryptography and hardware security firms to validate our security claims.
Firmware Security Audit
Independent review of cryptographic implementations, transaction signing logic, and attack surface analysis by specialized blockchain security firm.
Hardware Security Assessment
Physical security testing including side-channel analysis, fault injection resistance, and tamper-evidence validation by hardware security laboratory.
Penetration Testing
Red team assessment attempting real-world attack scenarios: supply chain compromise, malicious firmware injection, social engineering, and physical device attacks.
Ongoing Bug Bounty
Public bug bounty program rewarding security researchers who responsibly disclose vulnerabilities. Continuous community security validation.
Transparency Commitment
All third-party security audit reports will be published publicly on our website-including any identified vulnerabilities and our remediation responses. We believe security through transparency, not obscurity.
Industry Security Standards Compliance
Vaultix targets the highest security certifications in the hardware wallet industry, demonstrating commitment to independently validated protection.
| Standard | Description | Vaultix Status |
|---|---|---|
| EAL5+ Certification | Common Criteria Evaluation Assurance Level 5+ for Secure Element chip. Validates resistance to advanced physical attacks and side-channel analysis. | 🎯 Planned |
| FIPS 140-2/3 | Federal Information Processing Standard for cryptographic modules. Required for government and institutional use cases. | 🎯 Target Compliance |
| OSHWA Certification | Open Source Hardware Association certification for transparent hardware schematics and firmware. Enables community verification. | 🎯 Planned Post-Launch |
| CE/FCC Compliance | European and US regulatory certification for consumer electronics safety and electromagnetic compatibility. | ✓ Pre-Launch Requirement |
| RoHS Compliance | Restriction of Hazardous Substances directive for environmental safety and responsible manufacturing. | ✓ Manufacturing Standard |
Description
Vaultix Status
Why Certifications Matter
EAL Certification validates that the Secure Element chip has been independently tested against documented attack methodologies by accredited security laboratories. Higher EAL levels (5+ and 6+) indicate resistance to attacks requiring specialized equipment and expertise.
FIPS Certification is mandatory for hardware protecting government data and increasingly expected by institutional cryptocurrency holders. FIPS 140-3 validates cryptographic correctness, key management, and physical security.
OSHWA Certification demonstrates commitment to open-source transparency, allowing the security community to verify our hardware design matches our security claims. This prevents hidden backdoors or security weaknesses.
Supply Chain Security: From Factory to Your Hands
Hardware wallet supply chain attacks are a documented threat. Vaultix implements multi-layer anti-tampering protections to ensure the device you receive is authentic and uncompromised.
Secure Manufacturing
Vaultix devices manufactured in security-audited facility with access controls and surveillance. Each device receives unique cryptographic identity signed by Vaultix root certificate during manufacturing. Firmware checksum recorded for verification.
Tamper-Evident Packaging
Multi-layer tamper-evident seals on product packaging. Holographic authentication label with serial number linked to device cryptographic identity. Packaging designed to show visible damage if opened and resealed.
Shipment Integrity
Direct shipping from Vaultix-controlled warehouse-no third-party fulfillment centers with unauthorized access. Tracking numbers provided for chain-of-custody verification. Anonymous shipping addresses supported for privacy.
First-Boot Verification
On first power-on, Vaultix displays device cryptographic identity and firmware checksum on screen. Companion app verifies device signature against Vaultix certificate authority. Users can independently verify firmware integrity before generating wallet.
⚠️ Never Purchase from Unauthorized Resellers
Only purchase Vaultix hardware wallets directly from vaultix.com or verified authorized retailers listed on our website. Devices sold on secondary marketplaces (eBay, Amazon third-party sellers, Craigslist) may be counterfeit or tampered with.
If you receive a Vaultix device with damaged tamper-evident seals, pre-initialized wallet, or firmware verification failure-do not use it. Contact Vaultix support immediately for replacement.
Secure Your Spot on the Waitlist
Join thousands of security-conscious investors protecting their digital assets with Vaultix. Reserve your device for early access pricing and priority shipping.
Join Pre-Order Waitlist - No Payment RequiredExpected delivery Q3/Q4 2026 • Limited first-batch allocation